Public trust in the ability of many organisations to protect customer details is in freefall. So why do so many still rely on inadequate traditional defences, such as a firewall or anti-virus systems? Neil Hodge investigates
Trawl the internet and you’ll find a glut of horror stories about the impact cyber risks can have on an organisation. At best, an employee’s computer screen freezes momentarily: at worst, customer data is stolen and misused, and the organisation’s IT systems grind to a halt. That’s then compounded with regulatory censure, fines and public trust ripped to shreds.
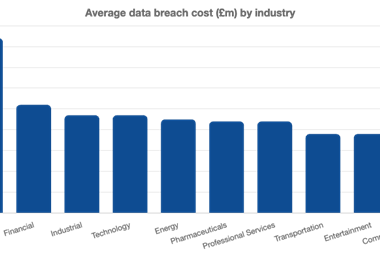
It has always been difficult until now to assess the cost of losing customer data, other than any fine incurred. However, the Ponemon Institute, a data protection and privacy research organisation, has released The 2009 Annual Study: UK Cost of a Data Breach, a new report that suggests a figure of £64 (e77) as the average cost to an organisation caused by the loss of each single customer record. Nearly half of that is attributed to lost business as consumer trust dips.
Lack of trust Public trust in the ability of organisations to handle their data is in freefall. In a recent UK survey conducted by database security company Guardium, nearly three-quarters of respondents (72%) said that they had concerns over their banks’ ability to safeguard financial data from internal threats and disgruntled employees. The government fared even worse, with just 2% of those surveyed having “complete trust” in government organisations to keep their data safe. Retailers also did badly, particularly in Europe: 88% of French and 64% of German respondents said that they were the least trusted organisations to safely handle consumer data.
To restore public confidence – and given the number of high-profile failures to protect consumer details – the USA and UK have beefed up their approach to enforcing data protection legislation.
The new US Data Accountability and Trust Act requires any organisation that experiences a breach of electronic data containing personal information to notify the victims. They must also inform the Federal Trade Commission, the US consumer protection agency. In addition, organisations have to designate an information security officer and establish a data security policy.
The UK has also given its data regulator new powers to force organisations to take data protection and privacy issues more seriously. As of last April, the Information Commissioner has new powers to issue fines of up to £500,000 for serious breaches, as well as the ability to conduct compulsory audits in central government departments where breaches may have occurred – though this is likely to be extended to all organisations soon.
Previously, the Information Commissioner’s Office (ICO) was unable to fine an organisation for a data breach; it could only censure it for doing so.
However, other regulators such as the FSA have levied fines – such as the £1.26m penalty against Norwich Union in 2007 – for failing to protect customer data adequately. To warrant a fine, the commissioner must be satisfied that there has been a serious breach likely to cause damage or distress, that the breach was either deliberate or negligent, and that the organisation failed to take reasonable steps to prevent it.
Law firm Morrison & Foerster partner and head of its EU privacy group, Ann Bevitt, says that until now the ICO has been a largely toothless regulator, as it had no real punitive powers. “That is beginning to change and organisations need to be aware of that. Organisations will be very keen to see how the regulator flexes its new muscles in the coming months: the expectation is that it will be looking for a few high-profile scalps to warn others,” she says.But it appears that organisations are still not taking cyber threats as seriously as they should, and that they are not reviewing their internal controls as rigorously as is necessary. “Too often, management is lulled into a false sense of security because they’ve deployed traditional perimeter defences such as firewalls, and they’re passing their audits,” Guardium vice-president of security strategy Phil Neray says. “However, it’s clear that this is no longer sufficient.” Nowhere is this clearer than in the painful case last January of US payment-processor firm Heartland.
The company was the victim of the largest data breach in history after a SQL injection attack – a technique that exploits vulnerable websites by inserting malicious codes into the database that runs it – by cyber criminals in the USA, Latvia, the Ukraine and the Netherlands resulted in the theft of 130 million credit cards. But Heartland had deployed standard firewalls and anti-virus systems. The company had even passed the audit for the Payment Card Industry Data Security Standard.
‘Man in the browser’ attacks
Experts warn of a number of new cyber risks that are becoming common, including the so-called ‘man in the browser’ (MITB) attacks. In these, the fraudster embeds an application within the browser that can detect and change information as the user enters transaction information online. As a result, the user believes that he is performing a valid transaction while the hacker changes the amounts and account numbers. According to IT analyst Gartner, MITB attacks present a serious threat to banking customers, but will migrate to other sectors within the next three years.
Increased dependence on ‘cloud computing’, whereby shared resources, software and information are provided to computers and other devices on demand via the internet, is also an area ripe for data loss, particularly since there are ‘public’ and ‘private’ clouds.
“Users should be aware of the concerns around security within the public cloud, which presents multiple customers with storage capacity and connectivity via a shared server environment,” says SunGard Availability Services chief strategy officer Dave Gilpin. “Many public cloud providers offer standardised security policies irrespective of the client or sensitivity of data. Concerns are compounded by the nature of the public cloud, which often stores significant levels of potentially sensitive information in one location, making it particularly attractive to cyber hackers and attempted security breaches.”
Yet, while new cyber risks are being uncovered, some believe that risk managers should keep their focus on internal risks, rather than external threats.
One risk manager admits privately that he loves to read about cyber warfare, espionage and nefarious government agencies hacking into IT systems – “but someone leaving a briefcase full of work papers, a laptop and mobile phone in the back of a taxi is much more likely to happen”.
Accountants Scott-Moncrieff business technology and consulting partner, Robert Mackenzie, believes that organisations often do little to protect their data and IT controls because they believe that cyber threats are too “high level” to affect them.
“Often security vendors try to attract clients’ attention with details of the real, but hard to believe, threats that the ordinary business person finds hard to relate to,” he says. “There are gangsters using hackers to attack businesses and extort money; there are foreign government sponsored attacks on western infrastructure; Google and Microsoft have been hacked and damaged. However, these are all easy to dismiss as happening to someone else and not what would happen to ‘our’ business.”
Be aware of ‘ordinary’ threats
Instead, says Mackenzie, organisations should try to stamp out the most obvious faults – people losing unencrypted USB data pens and laptops, and employees having available access to sensitive information. “Management needs to be made aware of the more ordinary and everyday threats that can cause real damage to their business,” he says. “These are the ones they are more likely to relate to and more importantly do something about.”
Other experts agree that it is largely the same risks that are still causing problems. Software testing provider SQS Software Quality Systems’ market director, Rob McConnell, says that the “threat landscape” has not changed significantly since the proliferation of mobile computing. “The same types of risks are continuing to threaten the confidentiality, integrity and availability of information and supporting ICT systems,” he says.
“These largely boil down to physical loss and theft of IT equipment – such as laptops and smart phones – malware, including worms and ‘Trojan’ networks such as ‘botnets’, and criminal activity, such as external system hacking and e-mail scamming. Half the battle is getting people to use common sense and think about the possible threats to information and the potential consequences.”
Risk management consultancy Control Risks’ associate director for information security, Ian McGurk, believes that cyber risk management has to be approached as a business risk issue. “Isolating IT risk to the IT department is counter-productive.
IT security is an issue that affects the whole organisation. It needs to be led by the board, it needs to involve everyone – and it needs to re-examine the most basic IT controls,” he says.
Some of the simplest controls can pay dividends – for example, changing passwords regularly. Bill Carey, vice-president of marketing and business development at Siber Systems, which produces password management software, says that the risk of security breaches most often comes down to the practices of individual employees, with 68% of Britons admitting that they use the same password many times, as it is too difficult to remember logins.
“With the increase in identity fraud cases – up by 74% in the last year – and e-crime practices such as phishing or key-logging on the rise, good password management is a basic security need for any organisation, yet it is one that is often severely overlooked,” he says. “An effective password policy – coupled with some basic user training – can make strong password management a lot easier and can protect against unauthorised access to your corporate network.”
Postscript
Neil Hodge is a freelance writer


















No comments yet