You might think your intellectual property is safe, but cyber crime is a fast-growing threat. Here are 10 steps you can take to protect your company’s deepest secrets
It’s your company’s most valuable asset: a technological breakthrough, a unique database, a list of important clients, a project under development. Whatever it may be, it has taken years or decades of work and investment. Yet it can be taken in a moment by cyber criminals.
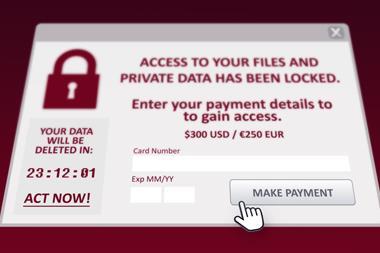
Commercial cyber crime is growing at an exponential rate around the world. In the UK, the combined loss to businesses of intellectual property theft and industrial espionage alone is £9.2bn a year, although “the real impact of cyber crime is likely to be much greater”, says a government-commissioned study by Detica.
Commercially useful ideas, designs, methodologies and trade secrets are all on cyber criminals’ hit list. “If a product is attractive to somebody on the outside, it’s under threat,” says Stuart Poole-Robb, chief executive of risk specialist KCS Group.
No business with saleable intellectual property is safe, says Will Thomson, director of Cardiff-based 4Secure. “Companies ask ‘why would anybody come after us?’” he says. “I tell them to look at what they’ve got that somebody else might want.”
The utilities, medical, pharmaceutical, media, software, financial, electronics and telecommunications sectors are particularly at risk. But the fact is that any intellectual property-rich organisation where transaction volumes are high may be considered a target for highly professional, IT-savvy cyber criminals working from anywhere in the world.
And although industry professionals say there’s no single solution – “all organisations are different” points out Thomson – there are several simple measures that can and should be taken.
1 Value your assets
Start by conducting an audit of all the company’s intellectual property and assessing its external value. KCS Group managing director Massimo Cotrozzi says: “Many companies have no idea what their level of risk is.” Typically, even those that do attempt to put a price on intellectual assets they think are at risk from cyber crime often make the mistake of under-valuing those they may not consider important, but which others will for different reasons.
2 Draw up a budget
Draw up a protection budget that bears a sensible relationship to the value of the property. “Many companies have ridiculously low budgets that are not comparable with the importance of the business involved,” Cotrozzi says. “Obviously it makes no sense to protect a £1bn formula with a £100 bit of software.”
3 Get tech savvy
Don’t think the company is safe just because it’s got all the latest firewalls and other software. “Anti-virus software can’t defend itself against viruses it doesn’t know about,” Poole-Robb explains. “The best gateway into a company is an email address.”
The big danger may not be inward traffic anyway. As Thomson says, “companies focus too much on what’s coming in instead of on what’s going out.”
4 Erase sensitive data
Recovery specialist Kroll Ontrack says that more than half of all firms leave commercially useful information on old computers and hard drives. A Ponemon Institute study, sponsored by Symantec, in March 2011 said: “The average data breach incident cost UK organisations £1.9m, or £71 per record.”
5 Protect your data
Push data protection disciplines throughout the company, for instance, by forbidding employees from using obvious passwords because hackers always work their way through a disciplined system based on our human foibles. And don’t leave passwords in obvious places.
6 Stick to the code
Too few companies have strict codes of online conduct backed up by effective enforcement, says 4Secure’s Thomson. “Employees always try to circumvent the system,” he says. Much cyber stealing can start from Hotmail, Gmail, flash files and other documents downloaded onto the desktop.
7 Check your staff
Run short-term or contract staff through a security check. It’s not uncommon for a cyber criminal to get through the door as a replacement cleaner or employee. “Checks on short-term workers are usually inadequate,” Poole-Robb says.
8 Need-to-know
Throw a ‘security perimeter’ around the company. Intellectual property should be assigned levels of importance according to its external value and made available on a need-to-know basis. Thus only designated employees should take designated data into an unsecured wider perimeter.
9 Mobile protection
Develop a mobile phone policy. Mobiles often contain important data, but are often badly protected.
10 Treat data with care
The most sensitive data should be treated like pure gold. The biggest private equity firms only release details about a major investment in a fully protected room where nothing can be downloaded, copied or removed.