Poor protection of vulnerable people and inefficient information sharing are hampering efforts to tackle cyber fraud
Research by the Royal United Services Institute (RUSI) reveals that organisations are failing to keep up with the rapidly-evolving cyber threat landscape.
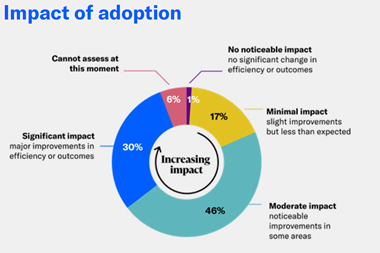
Seventy percent of respondents polled said they felt that the increase in remote working has not been matched by increased efforts from businesses to improve their cyber security and anti-fraud protection.
While the extent of the pandemic’s impact remains unclear, the report states that ‘the coronavirus pandemic has undoubtedly had an impact on the cyber fraud threat landscape’, detailing examples of how organised crime groups capitalised on vulnerabilities in both the business and government responses to the pandemic.
Either way, 44% of respondents believe that protecting vulnerable people is the most significant challenge in tackling cyber fraud.
The problem of information-sharing is also compounded by the ‘contrasting levels of prioritisation’ between stakeholders in the public and private sector.
The report outlines four key criteria that information-sharing partnerships should have: permanence, scalability, reciprocity, and multi-functionality. It judges that none of the current arrangements fulfil all four criteria.
And there is a general apathy towards information sharing mechanisms with 52% of respondents believing that they are poor or very poor.
RUSI raises the alarm about the distinct lack of coordination or common direction in the fight against cyber fraud. It says the effort is hampered by ‘inefficient’ information-sharing between law enforcement agencies and the private sector.
“Government authorities, law enforcement agencies, financial institutions, private sector industry associations, and cyber security and technology companies all hold information relevant to the detection and investigation of cyber fraud, but have no effective way of pooling it together,” is the conclusion.
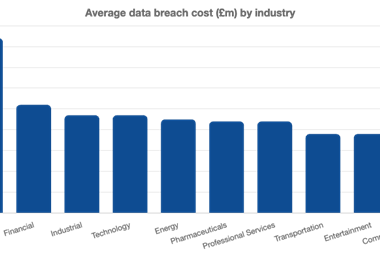
This problem is exacerbated by the various stages in the ‘life cycle’ of cyber fraud, from data breach to data exploitation and concluding with the laundering of proceeds. Each stage presents ”pinch points for financial institutions and law enforcement agencies to detect and prevent the successful commission of the crime”.
Entitled The UK’s Response to Cyber Fraud: A Strategic Vision, the report is based on in-depth research, and features an exclusive survey of UK law enforcement agency and financial services personnel.
The report makes 11 recommendations, including:
- That the National Crime Agency and City of London Police should boost their ‘pursue’ activities to include a more prominent role for pre-emptive technical takedowns of cyber frauds.
- Prosecutions and arrests must remain a core part of the overall law enforcement approach to raise the risk and reduce the rewards of committing cyber fraud, but only where there is a realistic chance of securing convictions or recovering the proceeds of crime.
- The National Police Chiefs’ Council should work with the Home Office to implement a set of key performance indicators for cyber fraud policing. This will consolidate the value of an effective ‘protect’ function for actual and potential victims, and a ‘prevent’ function focused on deterring potential criminals and reoffenders.
- The National Crime Agency, in consultation with the Information Commissioner’s Office, should publish comprehensive guidance for private sector organisations on how they can assist law enforcement in preventing and investigating cyber fraud through information sharing.
- The National Economic Crime Centre should take primary responsibility for ensuring that at least one of the relevant information-sharing programmes satisfies four key criteria in sharing data on cyber fraud threat actors: permanence; scalability; reciprocity; and multi-functionality.
- It also calls on the National Crime Agency, City of London Police, UK Finance and Cifas to convene partners for a pilot initiative focused on more effective integration of cyber, anti-money laundering and fraud data, with a view to elaborating examples of best practice.


















No comments yet