Criminals will continue to target high-profile organisations, having researched their ability to pay a ransom prior to the attack
Gangs of cyber criminals, organising themselves along the lines of drug cartels, are changing the ‘rules’ of ransomware attacks to keep ahead of the authorities’ efforts to thwart their activities, according to a report by CyberCube.
The cartels, formed to execute attack campaigns collaboratively, are expanding the playbook used by hackers to include so-called ‘double-extortion’, data exfiltration and data modification, it finds.
In 2021, cybercriminal cartels behind ransomware payloads will be responsible for the majority of attritional losses in the insurance market, and potentially even aggregation events due to cyber-attacks.
Darren Thomson, CyberCube’s head of Cyber Security Strategy, said: “Cyber criminals are continuing to adjust and improve their ransomware approaches in response to increasingly sophisticated cyber defence – and to reap as much reward as possible.
“What we’re seeing now is the rise of cyber cartels – loose affiliations of criminal hackers intent on gaining the maximum amount of money possible. They’re doing this by introducing new tactics into their attacks. This keeps them ahead of advances in security and allows them to extort money not once but twice.”
Criminal cartels are expected to continue to target high-profile organisations, including Fortune 500 companies, having researched their ability to pay a ransom prior to the attack. In addition, the techniques used to conduct these attacks are becoming more sophisticated and more targeted in the 2021 period.
In a double extortion attack, the report says, hackers not only encrypt the victim’s data, but also copy it to one of their own servers. Once the victim has paid the ransom, the cyber cartel still has the data in its possession, which it can use for the purpose of further extortion. Double-extortion first appeared in 2019 and gained popularity in 2020.
Criminals are also starting to threaten data integrity through data modification. In these attacks, the criminals tell the business that element of their data has been altered. These attacks are likely to become increasingly prevalent in the next few years and will focus on sectors utilising sensitive data such as healthcare and financial services.
There are now many prolific double-extortion ransomware cartels – Maze, REvil, Sodinokibi, DoppelPaymer, Nemty and more – creating their own websites where they publish data stolen from non-paying victims.
Other newly emerging ransomware-related threats include the development of ransomware worms – malware that can spread without human interaction – and increasing focus on so-called ‘single points of failure’ (SPoFs).
SPoFs are systems and services common to many thousands or millions of users and have the potential to affect large swathes of businesses. The recent attacks on Microsoft Exchange are a good example of this type of SPoF attack.
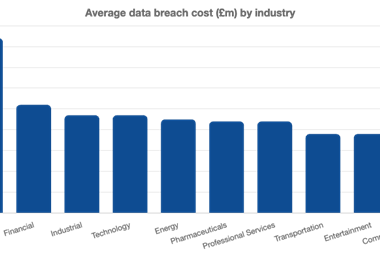
According to Security Boulevard, 337 confirmed ransomware events also resulted in a data breach in 2019. That number doubled to 676 in 2020.


















No comments yet