Social engineering attacks are on the rise, but losses can pose a grey area where insurance is concerned
Not every cyber attack is a sophisticated assault committed by hackers using the latest technology to break into digital infrastructure. Organisations often fall victim to so-called social engineering attacks, which prey on human vulnerabilities to access sensitive information or break into systems.
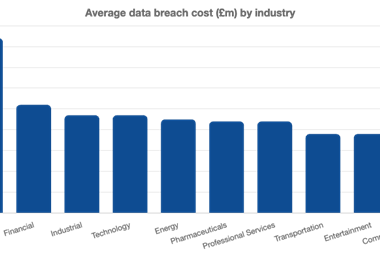
Last year saw a host of high-profile cyber attacks using social engineering techniques. According to Marsh, banks fended off nearly three times as many social engineering and phishing attacks in Asia alone.
In the early part of the COVID-crisis, cybercriminals were quick to manipulate natural fears and anxieties relating to the pandemic. A more dispersed workforce, with organisations rushing to adapt their networks to support lockdown working, also introduced vulnerabilities from a security standpoint.
“Social engineering is on the rise,” says Magda Chelly, head of cyber advisory at Marsh. “It is not a new threat and historically it does not involve sophisticated system ‘hacking’ activities. However, its techniques and complexity are improving every day, and cybercriminals can trick even the most cautious individual. As a result, this type of attack can have disastrous consequences for businesses and individuals who fall victim.”
In Singapore, prominent investor Barbara Corcoran, the founder of real estate brokerage company Corcoran Group, lost nearly $400,000 to a phishing scam in February last year. Criminals pretended to be her assistant and tricked the executive into sharing financial details.
The best cyber defence software in the world won’t stop a successful social engineering attack. The attacks prey on individual mistakes and vulnerabilities. According to CybSafe, 90% of UK cyber breaches in 2019 were caused by some kind of human error.
On the alert
With a multitude of different risks, how can organisations reduce the threat of successful social engineering attacks? According to Marsh, businesses and individuals can take practical steps to boost their defences.
The broker says individuals need to be cautious when receiving communication online, even if it looks legitimate.
Chelly says organisations should introduce multi-factor authentication into login processes, particularly on external social media platforms such as LinkedIn, which host a growing volume of business-related communication.
She adds: “Always verify the sender’s identity through a different channel of communication. If you received a payment request that you were not expecting or with an updated banking account, ensure that you have a process to verify the legitimacy of that request by using a different channel.
“For example, if the request was received through email, do not verify the request over email as it might have been compromised; use the phone or another channel and call the requestor.”
The firm also warns people against clicking on suspicious attachments received over email, and says antivirus and antimalware programmes cannot detect every kind of malicious attack. Finally, it calls on individuals to report suspicious activities as soon as possible.
Employee training is a large part of the defence against social engineering attacks. Cyber experts say companies need to train their employees in fraud prevention, and communicate with them about the latest techniques employed by cyber criminals.
Employees can be armed with knowledge about virtual private networks, strong passwords, and firewall protections to guard against risks.
Jennifer Tiang, regional cyber leader for Asia at Willis Towers Watson, says: “Company’s employees are both the weakest link and best defence for social engineering type attacks. Internal prevention techniques and frameworks to formalise processes will minimise the risk of human error and negligence.”
Gaps in cover
Can insurance play a part in guarding against social engineering risks? Tiang says insurers often regard social engineering fraud losses as falling under crime policies.
Organisations need to therefore review their insurance coverage with their broker, as some crime policies may not cover certain attacks.
“We caution that coverage of social engineering losses can pose grey areas, since the wording of some crime policies may be from a pre-digital era that didn’t envision the kind of online fraud that social engineering entails. We would encourage companies to work with their broker to check and fully understand coverage and what is or isn’t within scope.”
The coverage of social engineering losses under a cyber policy is “even more restrictive”, and “characterised as a minimal add on”, Tiang adds. “But for certain ‘best in class’ risks which can demonstrate robust controls, some coverage can be negotiated in [a] cyber policy.”
Tiang says social engineering fraud “is not something many insurers are jumping to insure or offer large limits on, but coverage is still available”.
She adds: “Many insurers are approaching this risk with caution by limiting the amount of coverage available for it and asking a series of in-depth questions around the organisation’s network security and standard operating procedures.
“As with all fraud and cyber risk, employees are the first and best line of defence. Constant training and awareness campaigns will always be the best way to prevent social engineering fraud in organisations.”


















No comments yet