C-suites and employees often think their business is not large or important enough to be hacked, but cyber criminals are not concerned about economies of scale

Workplace complacency continues to be a major contributing factor to the vulnerability of a business to cyber attack. Experts say although employees are aware of the risk, they do not comprehend the full scale of the impact that even a minor breach will have. One issue for risk managers is the misconception perpetuated by C-suites and employees that their business is not large or important enough to be hacked.
Darren Wray, chief executive of IT services firm Fifth Step, says cyber criminals are not concerned about economies of scale. “One of the crazy things we hear all the time is, ‘We’re too small to be of interest to the hackers’ or ‘We’ve got nothing interesting that the hackers want’ or ‘We’re too big to be of interest to the hackers because we’re too protected.’ That is just absolute nonsense. Many organisations are hacked because they have a piece of the jigsaw. It may be that your organisation holds the last five digits of the credit and that’s actually all the hacker needs in this instance. That’s where the complacency comes in.”
Here, then, are the top five cyber crimes businesses must be aware of.
Internal crime
This form of cyber attack will take place over a period of time, usually undetected, and involves a rogue employee gaining access to vital confidential information or taking control of part or all of the technology infrastructure. A ransom is usually demanded in exchange for surrendering control.
• Average detection costs for hiring forensic IT experts: $610,000 (Source: IBM/Ponemon Institute)
• Average lost business cost: $3.72m (Source: IBM/Ponemon Institute)
Organised cyber crimes targeting large multinationals, competitors and chief executives
Increasingly, spear phishing is being used by cyber criminals to gain access to a particular high-level employee in order to gain control of IT or accounting systems. Examples include an invoice attached to an email which, once downloaded, will contain a virus or malware that will take control of the firm’s systems. This form of attack is particularly dangerous because, due to its sophisticated nature, the employee may not be aware for a period of time that control has been lost.
• In 2015, spear phishing was responsible for 38% of cyber attacks on large enterprises (Source: Vanson Bourne survey)
• Average business cost of a spear phishing incident: $1.6m (Source: Vanson Bourne survey)
Ransomware and terror threats
A ransomware attack can create a two-pronged problem for businesses: pay the ransom to have the files unlocked or spend days rebooting systems from back-ups, which are likely to be out of date. In both scenarios, businesses are likely to face exhorbitant costs of business interruption, data recovery, lost sales or contracts, dissatisfied customers and traumatised employees.
In early 2015, the FBI issued an urgent alert to businesses globally about cryptographic ransomware – a particularly malicious type of malware that encrypts company data and demands payment for the decryption key.
• CryptoWall ransomware cost US businesses more than $18m in 2015
• 72% of infected business users were unable to access their files for at least two days following a ransomware attack.
Data theft, privacy and hacking
The aim of ‘hacktivism’, usually performed by social or political ‘hacktivists’, is to gain access to a firm’s sensitive records such as credit card data, social security information or medical records. Hacktivists usually pierce the firewalls and release the information publicly as a way of crippling the firm. They are mainly motivated by social or political justice, rather than monetary gain.
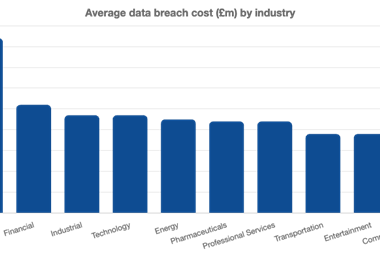
• Average cost per record breached: $230 (Source: IBM/Ponemon Institute)
• Cost of malicious attack per capita rose from $159 in 2014 to $170 in 2015 (Source: IBM/Ponemon Institute)
• Average post-breach costs: $1.64m (Source: IBM/Ponemon Institute)
Fraud
Fraud-motivated cyber attacks come in many forms. Unsecured databases mean employees or hackers, via social engineering methods, are able to gain access to businesses’ internal systems and use them for undetected fraudulent invoicing, bank transfers and incremental syphoning. This type of fraud can be particularly damaging to the reputation of a business because lax security instils a sense of fear in clients and can lead to legal action against the firm for failing to prevent unauthorised access to electronic data containing others’ confidential information.
• Average customer notification costs: $560,000 (Source: IBM/Ponemon Institute)
• Average legal defence costs: $698,000 (Source: IBM/Ponemon Institute)


















No comments yet