Analysis following the SolarWinds fallout shows there are three ways companies can build more resilient digital supply chains
In the fallout of the SolarWinds incident, it is crucial that all stakeholders in the supply and value chains embrace a risk-informed cybersecurity approach to ensure a secure and resilient ecosystem. This is according to World Economic Forum’s cyber and systems expert Georges de Moura.
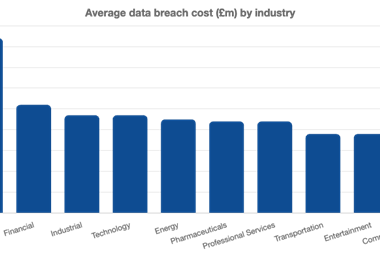
Global technology supply chains are increasingly diverse and complex, resulting in changes in the overall risk for critical systems that support national defence, vital emergency services and critical infrastructure.
de Moura notes that 60% percent of organisations worked with more than 1,000 third parties and 40% of manufacturers had their operations affected by a cyber-incident during 2019.
“The SolarWinds’ incident further reinforced the threat to global digital supply chains and the strategic imperative for public and private sector stakeholders to ensure trust in the digital ecosystem,” he says. ”It is critical that the software that drives the digital ecosystem is both trusted and secured.”
The following core principles will contribute to a more secure and resilient supply chain and help move the needle on mitigating this complex and multifaceted challenge:
1. Embed security and privacy in the procurement process and life cycle. Having a mature third-party risk-management policy and practice will ensure cybersecurity and privacy are constantly considered and addressed with mature, consistent, repeatable and effective measures.
2. Take a risk-based approach in assessments of third parties. A risk-based approach will help guide the third-party acceptance/rejection decision-making process, and helps efficiently and accurately mitigate cybersecurity threats third parties pose to the broader ecosystem.
3. Implement a source code policy and secure-by-design development. Such a policy aims to reduce the risks around the development, management and distribution of software and software source code, which must go beyond defending intellectual property and address customer impact. It will help protect and strengthen trust in the digital ecosystem so businesses, governments and individuals can all have trust in, contribute to and benefit from the digital economy.
The policy should apply to all source code written by or on behalf of an organisation and must ensure that any source code is not tampered with, does not contain any known unmitigated security vulnerabilities and contains a license that is compatible with the company’s other policies.


















No comments yet