Financial fines for manufacturing firms are up to €15m or 2.5 percent of global annual revenues under the CRA
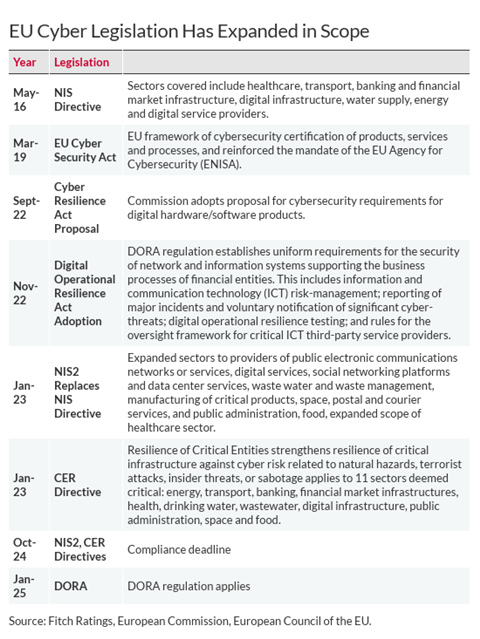
Key directives on critical and digital infrastructure have been introduced to strengthen the EU’s resilience against online and offline threats, from cyberattacks to crime, risks to public health or natural disasters.
NIS2, the Resilience of Critical Entities (CER) and the Digital Operational Resilience Act (DORA), recently came into force to bolster cybersecurity requirements to protect critical and digital infrastructure for applicable entities in member states.
The Commission is in the process of adopting the EU Cyber Resilience Act (CRA), with implications for manufacturing organisations. Introduced in September 2022 - consultation is ongoing and it has a proposed 24-month transition period.
Feedback from Siemens Healthineers emphasised the importance of ensuring “consistency between the requirements of NIS 2 Directive (for digital infrastructure) and CRA to avoid legal uncertainty and additional red tape”.
It suggests extending the transition period for CRA beyond the proposed 24 months as the scope of the proposed law is “very broad and encompasses a wide range of physical products”.
It also recommends lengthening the reporting period for security breaches to at least 72 hours, bringing it in line with the GDPR. ”The period for reporting should consider that cyberattacks are often complex and require the resource-intensive investigation of experts,” proposes the German medical devices company.
Strict rules for a connected world
The new rules could mean millions in fines for manufacturers, distributors and importers if they fail to prioritise cybersecurity embedded within IoT in an increasingly connected world.
The initiative aims to ”address market needs and protect consumers from insecure products by introducing common cybersecurity rules for manufacturers and vendors of tangible and intangible digital products and ancillary services”.
Manufacturers, distributors and importers are required to notify ENISA – the European Union’s cybersecurity agency – within 24 hours if a security vulnerability in one of their products is exploited. Exceeding the notification deadlines is already subject to sanctions.
The financial fines for affected manufacturers and distributors are up to €15m or 2.5 percent of global annual revenues in the past fiscal year – the larger number counts.
“This makes it absolutely clear: there will be substantial penalties on manufacturers if the requirements are not implemented,” says Jan Wendenburg, CEO of the cybersecurity company ONEKEY.
Protecting critical infrastructure after Nord Stream
The NIS2 Directive is intended to complement the CRA and significantly expands the sectors and type of critical entities falling under its scope.
The directive applies not only to critical infrastructure operators, but to organisations of all types and sizes. These include providers of public electronic communications networks and services, data centre services, wastewater and waste management, manufacturing of critical products, postal and courier services and public administration entities, as well as the healthcare sector more broadly.
“Many companies are still not clear to what extent NIS 2 affects their own operations,” warns Rainer M. Richter, Vice President EMEA & APAC at Horizon3.ai. ”The fact is that the law affects practically all companies, right up to the management level. Failures in cybersecurity must be identified and remedied as quickly as possible.”
The CER will strengthen the resilience of critical infrastructure to a range of threats, including natural hazards, terrorist attacks, insider threats, or sabotage.
11 sectors will be covered: energy, transport, banking, financial market infrastructures, health, drinking water, wastewater, digital infrastructure, public administration, space and food.
Following the acts of sabotage against the Nord Stream pipelines, on 5 October 2022, EU President von der Leyen presented a five-point plan for resilient critical infrastructure, now enshrined within the new legislation.
Key elements are: enhancing preparedness; working with Member States with a view to stress test their critical infrastructure, starting with the energy sector and then followed by other high-risk sectors; and strengthening cooperation with NATO and key partners on the resilience of critical infrastructure.
Tight time horizon
Member States have 21 months to transpose NIS2 into national law.
According to the EU, there is currently a ransomware attack every eleven seconds. In the last few weeks alone, among others, a leading German children’s food manufacturer and a global Tier1 automotive supplier, headquartered in Germany, were hit, with the latter becoming the victim of a massive ransomware attack.
The time horizon is also tight where the CRA is concerned, according to Wendenburg, ”considering that orders for IT products are already being placed with OEM manufacturers this year for the next 12-18 months.
”Therefore, the timing situation needs to be considered and resolved now, before a product ends up not being launched or delayed due to defects.
“The pressure on the industry – manufacturers, distributors and importers – is growing immensely,” he continues. “The EU will implement this regulation without compromise.”
A positive direction, says Fitch
The new regulations are directionally positive, according to rating agency Fitch Ratings.
Proper cyber hygiene and strong controls will not by themselves lead to positive ratings movement, although poor controls could result in negative rating actions if proven to be material to an entity’s finances and/or reputation.
A cyber event could increase regulatory scrutiny and litigation, it adds.
Compliance may be more difficult for small-to-medium companies in unregulated industries that lack robust cybersecurity infrastructure, putting them more at risk than critical infrastructure and large companies in regulated industries.
Cybersecurity budgets are increasingly under pressure amid reduced revenue outlooks, growing recessionary risks and economic uncertainty, which could increase the risk of attacks.


















No comments yet