The SolarWinds attack has awoken risk managers to the threat of Trojan-Horse type supply chain incidents
The imminent, ever-present danger of the cyber threat was put into sharp focus in December following one of the most sophisticated attacks in history.
In an attack described as “large-scale digital espionage”, hackers gained access to up to 17,000 targets through a trojanised attack on major third-party software provider SolarWinds.
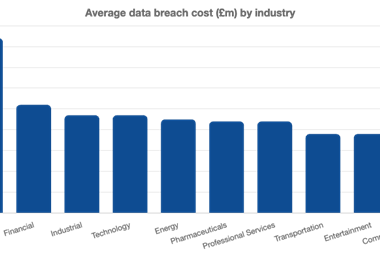
It could have been worse. The company had nearly 300,000 customers as of December 2020, nearly all of them Fortune 500 firms.
As it was, hackers gained a ‘backdoor’ to some of the world’s most prominent businesses and government departments. Tech giants, including Microsoft and Google, and US state agencies including the Treasury and State Department were compromised.
New victims continue to emerge as Solarwinds users undergo audits. IT Security vendors Mimecast, Palo Alto Networks, Qualys and Fidelis added their names to the victim list in late January.
Trojan horse
Hackers accessed the data of SolarWinds clients through a booby-trapped software ‘update’.
Cyber experts on both sides of the Atlantic have blamed the attack on Russian state-backed hacking collective Cosy Bear, though no criminal or state organisation has claimed responsibility.
The incident has highlighted the threat of Trojan-Horse type threats. While organisations may have cyber defence plans, IT structures and risk mitigation measures in place, companies remain vulnerable to attacks through third parties.
By targeting a software provider instead of an organisation directly, the SolarWinds hackers accessed a wider number of targets.
Risk experts say organisations must wake up to the threat of supply-chain cyber risks. The WEF Global Risks Report 2021 identified cybersecurity failures as a “clear and present danger” to the world economy, and one of the risks with the most significant impact.
According to Adam Selwood, the chief technology officer of Australia-based cybersecurity consultancy Cynch, “supply chains are clearly a target for motivated and sophisticated actors”. He adds: “Every technology carries risk, and there’s a higher risk when trust is given to tech.”
Selwood says companies can take steps to mitigate the risk of third-party hacks: ”The visibility of assets and suppliers is often lacking,” he says. Procurement practices, including discovery scans and monitoring, are vital, he adds.
Supply chain vulnerabilities
Julia Graham, deputy chief executive of Airmic, says backdoor, third-party attacks are “certainly becoming more frequent and more frequently reported”.
“The types of attacks we see employed are also constantly changing, alongside new technology, the changing economic backdrop and the opportunism of attackers.
“Perceptions about the cyber threats faced have changed. For example, the era of hackers perceived as disgruntled activists working alone is over. The range of malevolent actors also varies considerably, from organised crime theft to government-sponsored attacks designed to deny access to critical infrastructure.”
Graham says the SolarWinds attack is particularly alarming as most organisations are reliant on third-party technology providers.
“A key lesson will be to visit and revisit due diligence checks on essential service providers to ensure they have effective security in place,” she adds.
She warns regulators are likely to impose strict penalties on companies that fall victim to attacks through third-parties. More stringent regulatory regimes, such as GDPR, heighten the risk, she adds.


















No comments yet